Feedback Linearization and Self-Tuning PD Fuzzy Controller for Wheeled Mobile Robot
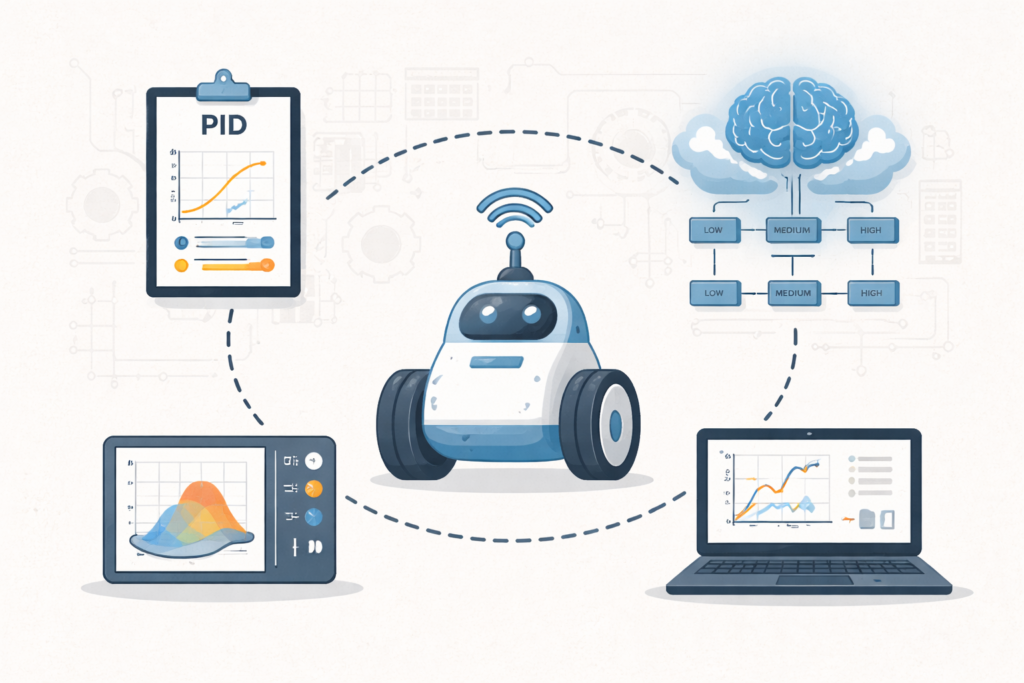
This research presents an intelligent control approach for wheeled mobile robots using feedback linearization combined with a self-tuning PD fuzzy controller. The method dynamically adjusts control parameters to handle nonlinearities and uncertainties in robot motion. By integrating fuzzy logic with conventional PD control, the system improves tracking accuracy, stability, and responsiveness. The proposed approach enhances […]
Critical Review: Fog Computing Dimensions for Data Security Features in Cloud-Based Applications
This review critically examines the role of fog computing in enhancing data security for cloud-based applications. By distributing computation closer to end devices, fog architecture improves access control, reduces latency, and limits data exposure to security threats. The study analyzes key security dimensions, including authentication, encryption, and intrusion detection, within fog-enabled systems. These insights highlight […]
Leveraging Cloud Technology for Enhanced Online Examination System

This study explores how cloud technology can enhance online examination systems by enabling secure, scalable, and easily accessible testing environments. With cloud-based storage and real-time synchronization, exams can be administered and monitored across multiple devices while maintaining consistent performance. The approach improves data management, reduces system failures, and ensures reliable exam delivery. Cloud integration also […]
A Comprehensive Study on Steganography and Text-to-Image Encryption Using RGB Substitution Techniques for Cybersecurity

This study explores the use of RGB substitution techniques to perform steganography and text-to-image encryption for cybersecurity applications. By embedding text within image color channels, the method conceals sensitive information while maintaining visual integrity. The research analyzes encryption strength, data-hiding capacity, and resilience against attacks. These techniques enhance secure communication, reduce detection risks, and support […]