Feedback Linearization and Self-Tuning PD Fuzzy Controller for Wheeled Mobile Robot
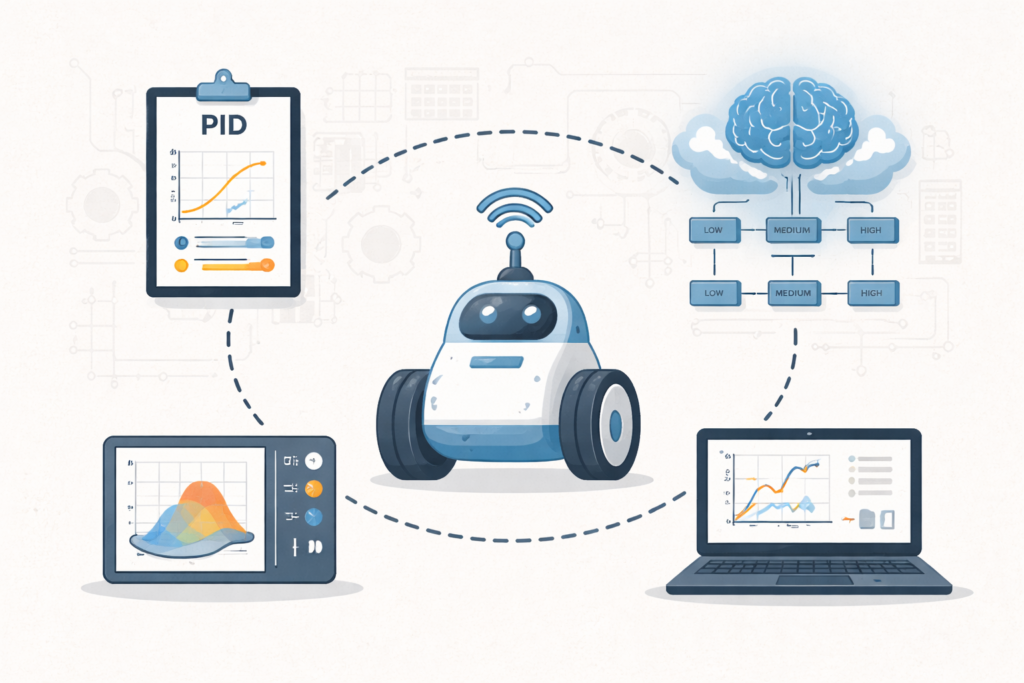
This research presents an intelligent control approach for wheeled mobile robots using feedback linearization combined with a self-tuning PD fuzzy controller. The method dynamically adjusts control parameters to handle nonlinearities and uncertainties in robot motion. By integrating fuzzy logic with conventional PD control, the system improves tracking accuracy, stability, and responsiveness. The proposed approach enhances […]
Critical Review: Fog Computing Dimensions for Data Security Features in Cloud-Based Applications
This review critically examines the role of fog computing in enhancing data security for cloud-based applications. By distributing computation closer to end devices, fog architecture improves access control, reduces latency, and limits data exposure to security threats. The study analyzes key security dimensions, including authentication, encryption, and intrusion detection, within fog-enabled systems. These insights highlight […]
Leveraging Cloud Technology for Enhanced Online Examination System

This study explores how cloud technology can enhance online examination systems by enabling secure, scalable, and easily accessible testing environments. With cloud-based storage and real-time synchronization, exams can be administered and monitored across multiple devices while maintaining consistent performance. The approach improves data management, reduces system failures, and ensures reliable exam delivery. Cloud integration also […]
A Comprehensive Study on Steganography and Text-to-Image Encryption Using RGB Substitution Techniques for Cybersecurity

This study explores the use of RGB substitution techniques to perform steganography and text-to-image encryption for cybersecurity applications. By embedding text within image color channels, the method conceals sensitive information while maintaining visual integrity. The research analyzes encryption strength, data-hiding capacity, and resilience against attacks. These techniques enhance secure communication, reduce detection risks, and support […]
Map Matching Algorithm: Curve Simplification for Frechet Distance Computing & Precise Navigation Using RTKLIB
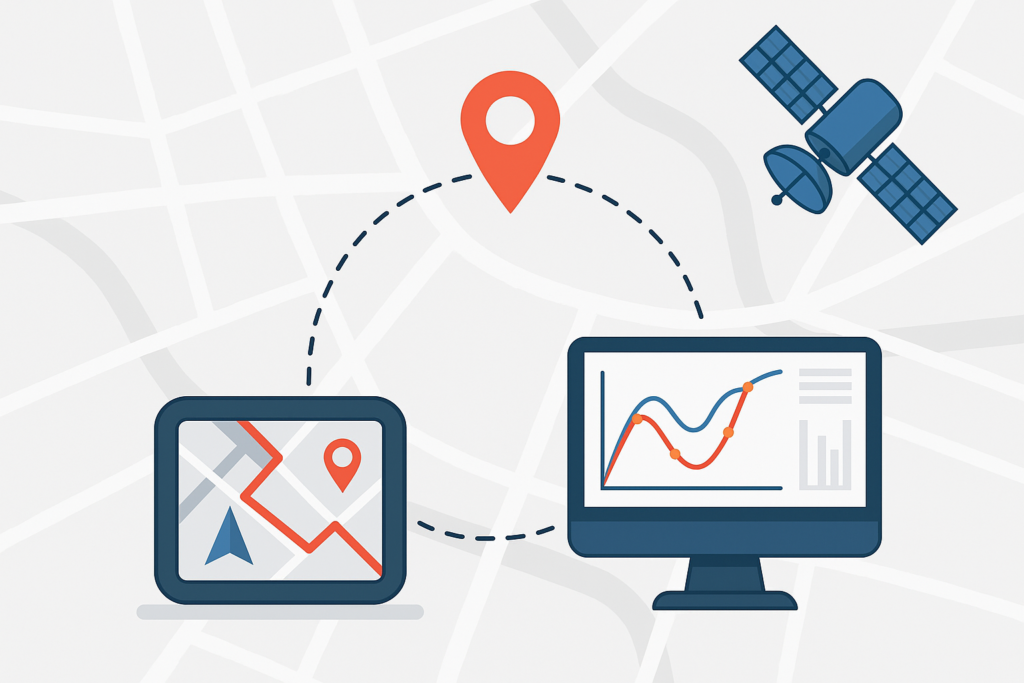
This study presents a map matching approach that combines curve simplification with Frechet distance computation to achieve highly accurate navigation results using RTKLIB. By comparing the vehicle’s trajectory with road network geometry, the algorithm identifies the most suitable path even in challenging urban conditions. RTKLIB integration offers enhanced GNSS precision, reducing positional errors and improving […]
Machine Learning–Based Biomedical Image Processing for Echocardiographic Images
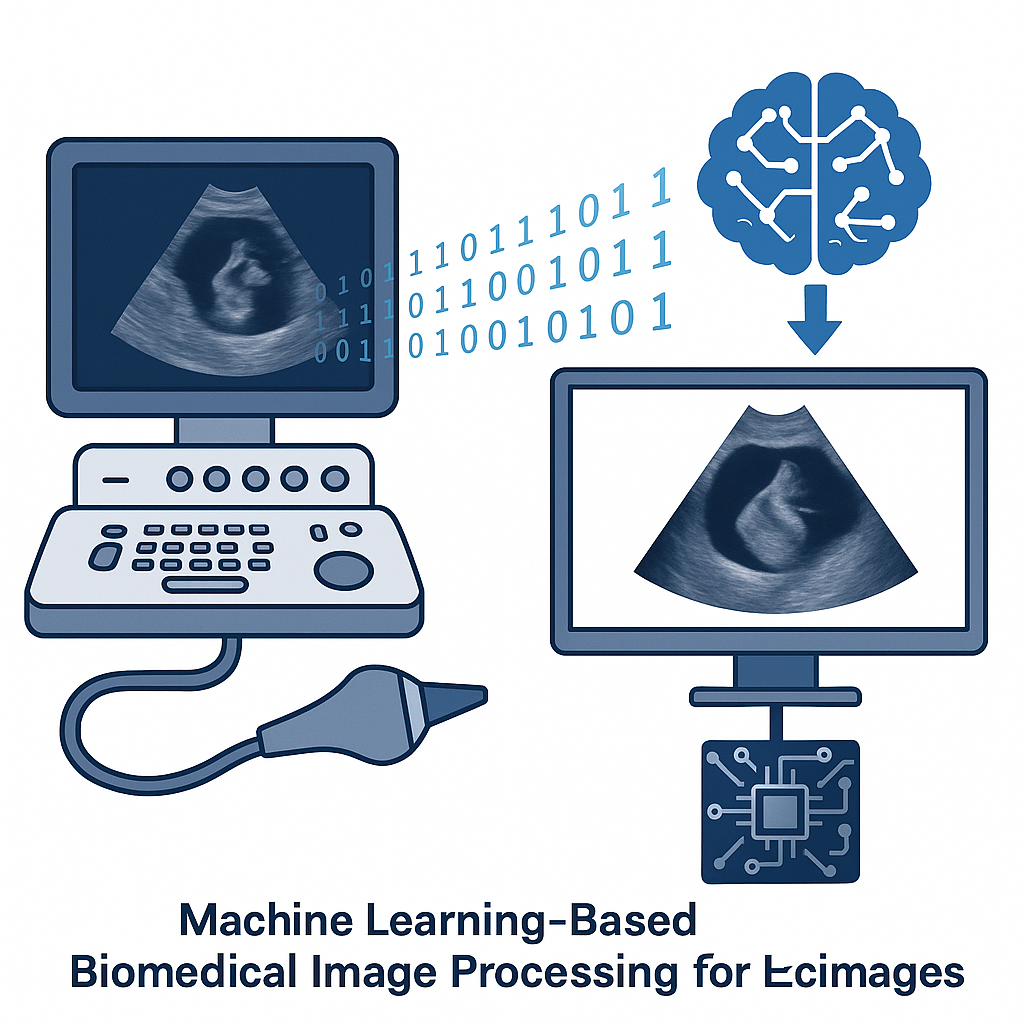
This research applies machine learning methods to enhance the quality and clinical usefulness of echocardiographic images. By leveraging algorithms for noise reduction, segmentation, and structural feature enhancement, the system produces clearer and more accurate heart images for diagnostic evaluation. The study demonstrates how machine learning can help clinicians identify cardiac abnormalities more efficiently, improving diagnostic […]
Correction to LTE-NBP with UWB-WBAN for Biomedical Applications
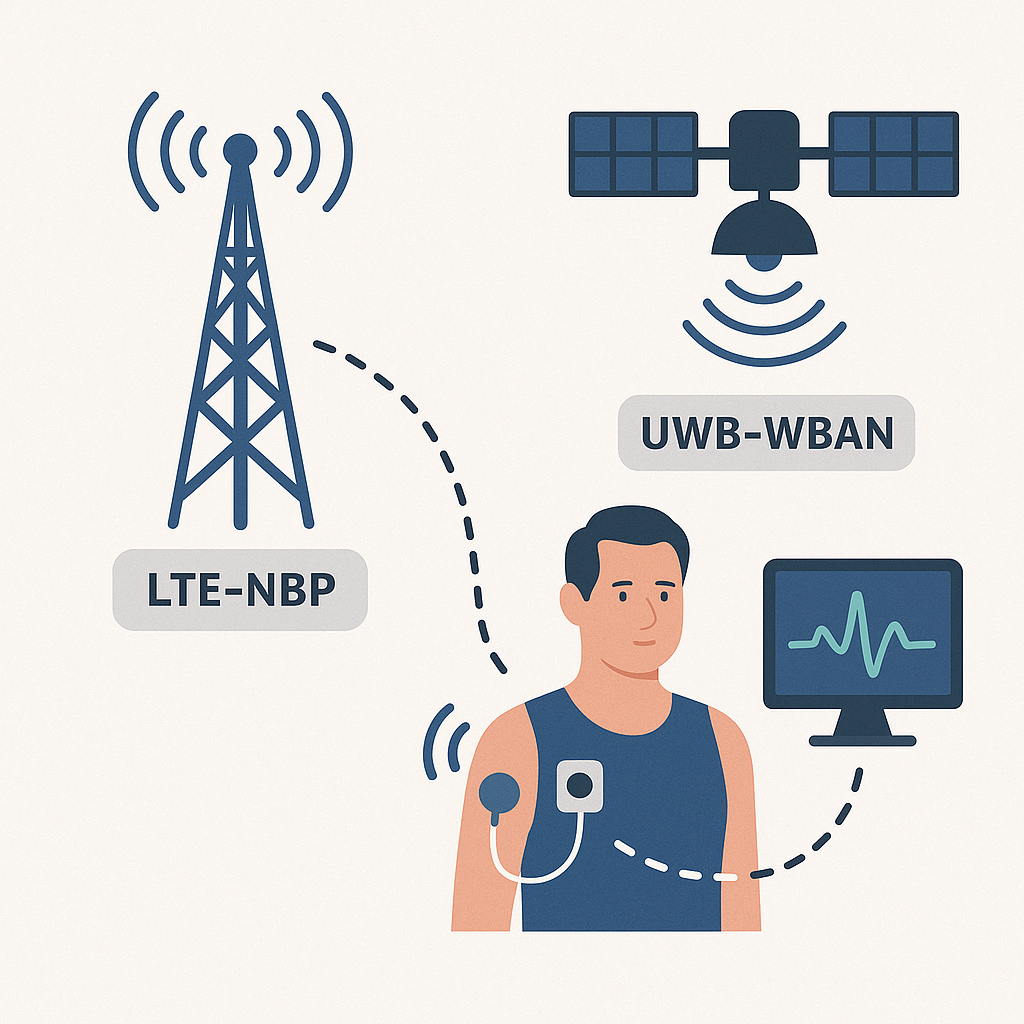
This study presents corrections to the LTE-NBP model integrated with UWB-based Wireless Body Area Networks for advanced biomedical monitoring. The revised approach improves communication reliability, signal stability, and data accuracy between body-worn sensors and medical monitoring systems. By optimizing the interaction between UWB and LTE-NBP technologies, the corrected model reduces transmission errors and enhances patient […]
Statistical Impact Analysis of Congestion Control Algorithm in MANET
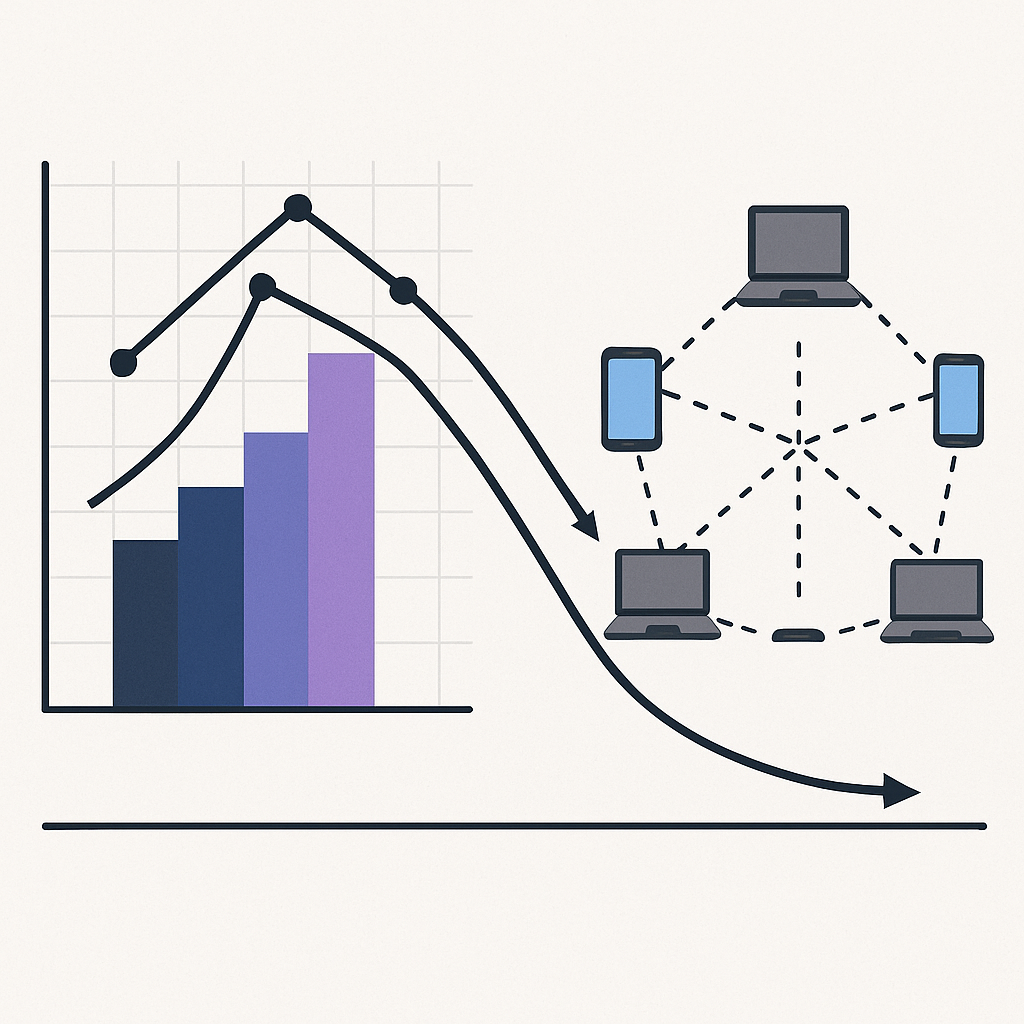
This study examines the statistical impact of congestion control algorithms within Mobile Ad-Hoc Networks (MANETs). By analyzing key performance metrics such as throughput, latency, packet loss, and network stability, the research evaluates how different algorithms respond under varying traffic loads. The findings highlight how congestion control strategies influence overall network efficiency and communication reliability. This […]
Stub Signature-Based Efficient Public Data Auditing System Using Dynamic Procedures in Cloud Computing

This research presents a stub signature–based system designed to improve the security and efficiency of public data auditing in cloud environments. By using lightweight, dynamically generated signatures, the framework enables third-party auditors to verify data integrity without accessing or exposing the original data. The approach reduces computation overhead, enhances privacy preservation, and ensures transparent and […]
Multiple Pattern Synthesis of Circular Antenna Arrays for Achieving Lower Side Lobe Level and Higher Directivity Using Hybrid Optimization Algorithm
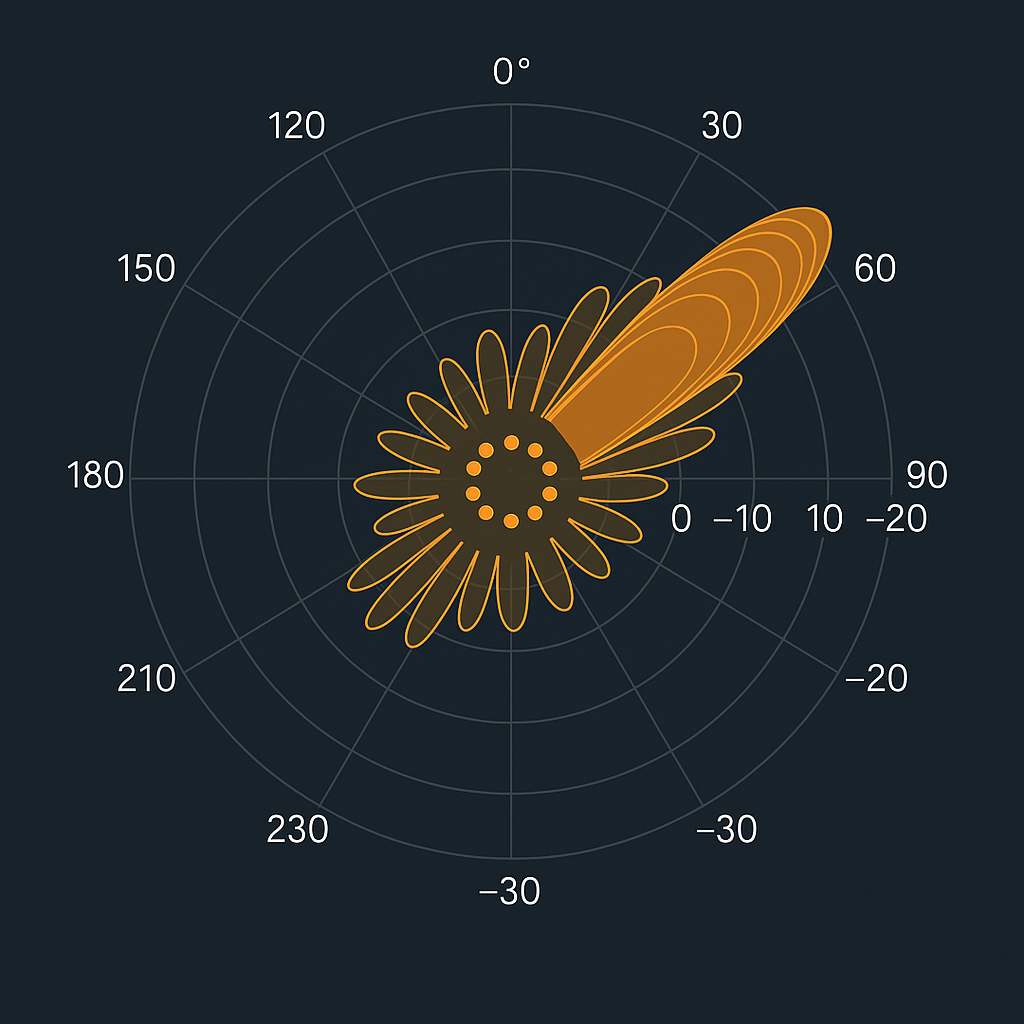
This study focuses on synthesizing multiple radiation patterns in circular antenna arrays using a hybrid optimization algorithm. The approach improves antenna performance by reducing side lobe levels and enhancing main lobe directivity. By combining advanced optimization methods, the system achieves precise control over radiation characteristics, making it suitable for high-efficiency communication and radar applications. The […]